Extracting strings is an important step in malware analysis. In this post we will concentrate on static analysis and learn how we can extract/interpret strings from malware. You can download Rokrat (MD5: b441d9a75c60b222e3c9fd50c0d14c5b) from VirusTotal / VirusBay / ANY.RUN.
Why do we need to do this?
- Guess the malware functionality based on the strings.
- If we google some of the strings, we may find some related articles/hashes online.
- Guess file type, compiler info, packer etc.
Tools
- Windows: Sysinternals Strings
- Linux: Install binutils e.g.
sudo apt install binutilsfor GNU strings utility - macOS: Inbuilt strings tool doesn’t cover the Unicode strings, it only extract the ASCII strings so we need to install GNU strings using
brew install binutils
How to extract?
For Linux/macOS, if you use GNU strings then use following command and default minimum length is 4
strings -a malware.exe. --> ASCII strings
strings -a -el malware.exe --> Unicode Strings
For Windows, I use strings from Sysinternals and default minimum length is 3
strings malware.exe --> ASCII and Unicode strings
Sysinternals Strings tool search for ASCII and Unicode strings in binary images.After you execute the tool without any parameter it will show you different options.
When strings is executed without any option it will extract Unicode and ascii strings with default string length of 3.
Steps
- strings <file_path> > output.txt
- Open output.txt in your favourite editor
Packed Dummy Rokrat strings
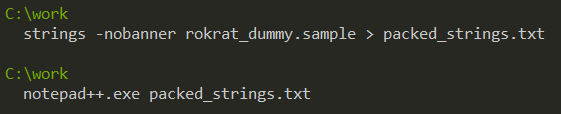
strings -nobanner rokrat_dummy.sample > packed_strings.txt
strings -nobanner -n 6 rokrat_dummy.sample > packed_strings.txt
It generated around 5014 strings, please go through the strings output(i.e. packed_strings.txt) before reading further and try to guess the usage.
Some observations from extracted strings
| Strings | Comments |
|---|---|
| .text `.rdata @.data .rsrc @.reloc | Section names |
| An application has made an attempt to load the C runtime library incorrectly. Please contact the application's support team for more information. R6033 - Attempt to use MSIL code from this assembly during native code initialization | Strings related to library code |
| >@| 3@| K@| &@| #@} | Some of the strings are not useful, you can ignore them |
| GetTempPathW VirtualAllocEx LockResource WriteProcessMemory | API name |
Few important strings
| Strings | Guess (or comments) |
|---|---|
| cmd.exe | Maybe it is using cmd.exe to execute some program? Maybe looking for this process name? |
| d:\HighSchool\version 13\2ndBD\T+M\T+M\Result\DocPrint.pdb | PDB Path: After googling, you may find related samples/articles |
| PST PDT photo.jpg Exif Adobe Photoshop CC 2017 (Windows) 2017:09:29 23:17:46 Adobe Photoshop CC 2017 | photo.jpg file embedded in the file? Made by Adobe photoshop CC ? 2017:09:29 23:17:46 May be creation date? |
Unpacked Rokrat strings
I have unpacked the b441d9a75c60b222e3c9fd50c0d14c5b sample and extracted the unpacked strings with minimum length 6.
strings -nobanner -n 6 unpacked_rokrat.sample > rokrat_unpacked_strings.txt
Few important strings
| Strings | Guess (or comments) |
|---|---|
| https://api.box.com/oauth2/token https://account.box.com/api/oauth2/authorize https://cloud-api.yandex.net/v1/disk/resources?path=%s&permanently=%s ... | Used as CC? |
| System manufacturer (Other) (Unknown) (Desktop) (Low Profile Desktop) (Mini Tower) .... | Collecting systeminfo and sending this info to CC ? |
| SbieDll.dll api_log.dll C:\Program Files\VMware\VMware Tools\vmtoolsd.exe ..... | Anti-analysis techniques |
What to look for?
- Domain names/IP address(or CC)
- Registry keys
- Network request pattern
- PDB path
- Directory/File path or name
- List of application names e.g Chrome, Firefox, Skype, FTP application etc.
- Malware analysis tools
- Any other unique strings
When will it fail?
- File is packed
- Strings are encrypted/encoded
- Maybe the file is just a downloader and CC are encrypted?
- Many others…..

1 Comment. Leave new
[…] via Extract strings – Securityinbits […]