In this last part, we will compare Old Qealler with the new Qealler/Pyrogenic variant. The previous posts Pyrogenic Infostealer static analysis – Part 0x1 & Unpacking Pyrogenic/Qealler using Java agent -Part 0x2 went through the latest Pyrogenic/Qealler [6] statically and dumping the unpacked code using Java agent.
CONTENTS
Brief Timeline
June 2018
First Old Qealler sample [4] (MD5: 65ab1ef8e9cef5c489d4b01cbb8a2a22) found on ANY.RUN
Jan-Feb 2019
Multiple cyber security company posted articles[3] about Qealler variant using the Qazagne Python credential harvester.
April 2019
Based on ANY.RUN submissions, Old Qealler variant using the Qazagne stopped around April 2019
Aug 2019 – Now
Based on ANY.RUN submissions, Qealler tagged samples started around Aug 2019 and continue till now Aug 2020.
Similarity between Qealler variants
For easy/fast comparison, I have imported unpacked code of both Qealler variant in Eclipse IDE. I will compare this Old Qealler (MD5: 8D564A18B902461C19936CCB1F4E2F12) [5] and new Pyrogenic/Qealler sample (MD5: F0E21C7789CD57EEBF8ECDB9FADAB26B) [6] used in the previous posts. Highly recommended to read through the existing analysis of Old Qealler Unloaded[2] by @jeFF0Falltrades & article [3] by Zscaler.
Both Qealler variants use the same Qrypter packer variant.
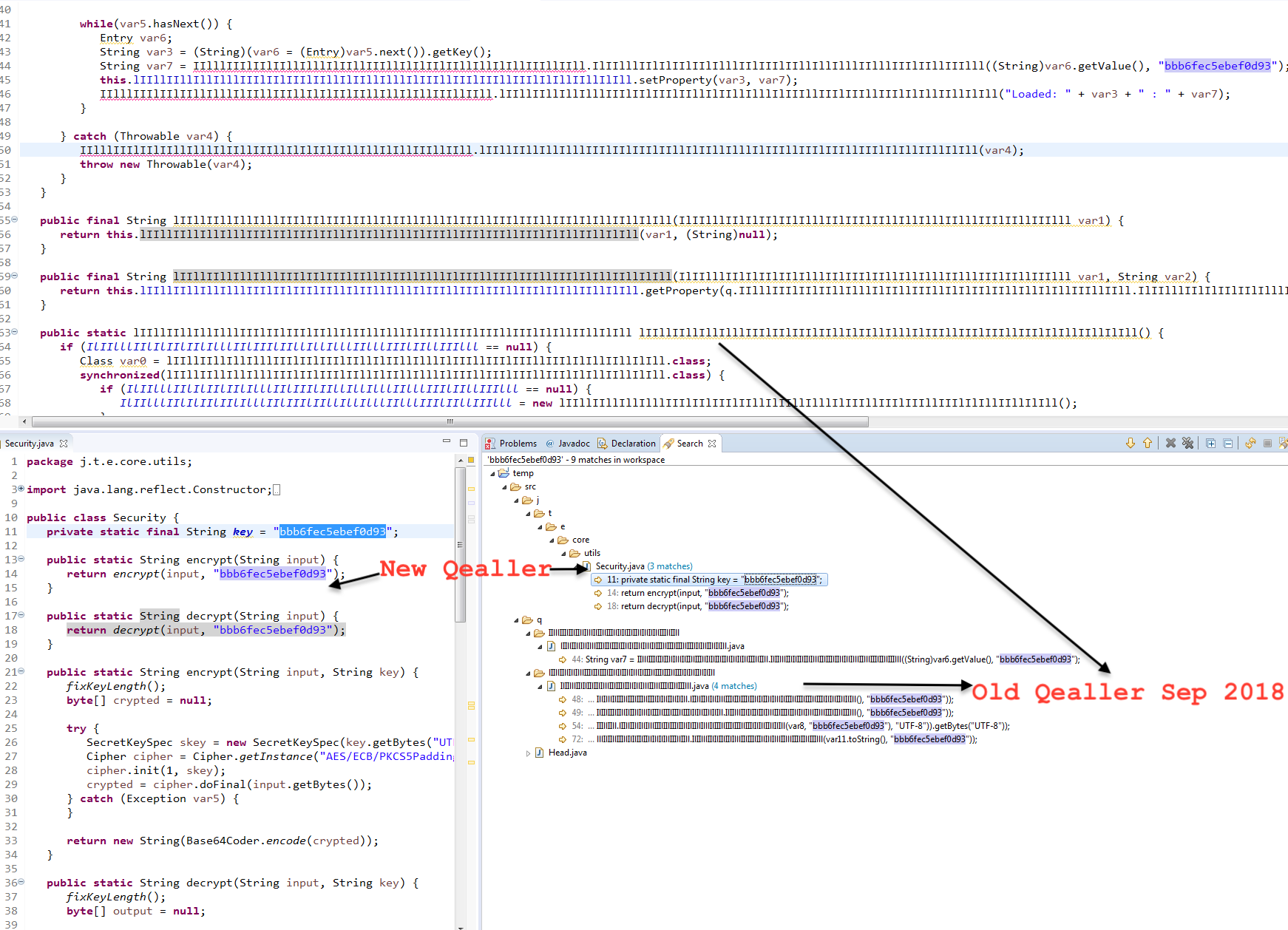
1. AES Key bbb6fec5ebef0d93
You will find multiple references to bbb6fec5ebef0d93 as shown below. This is the AES key used in both variant.
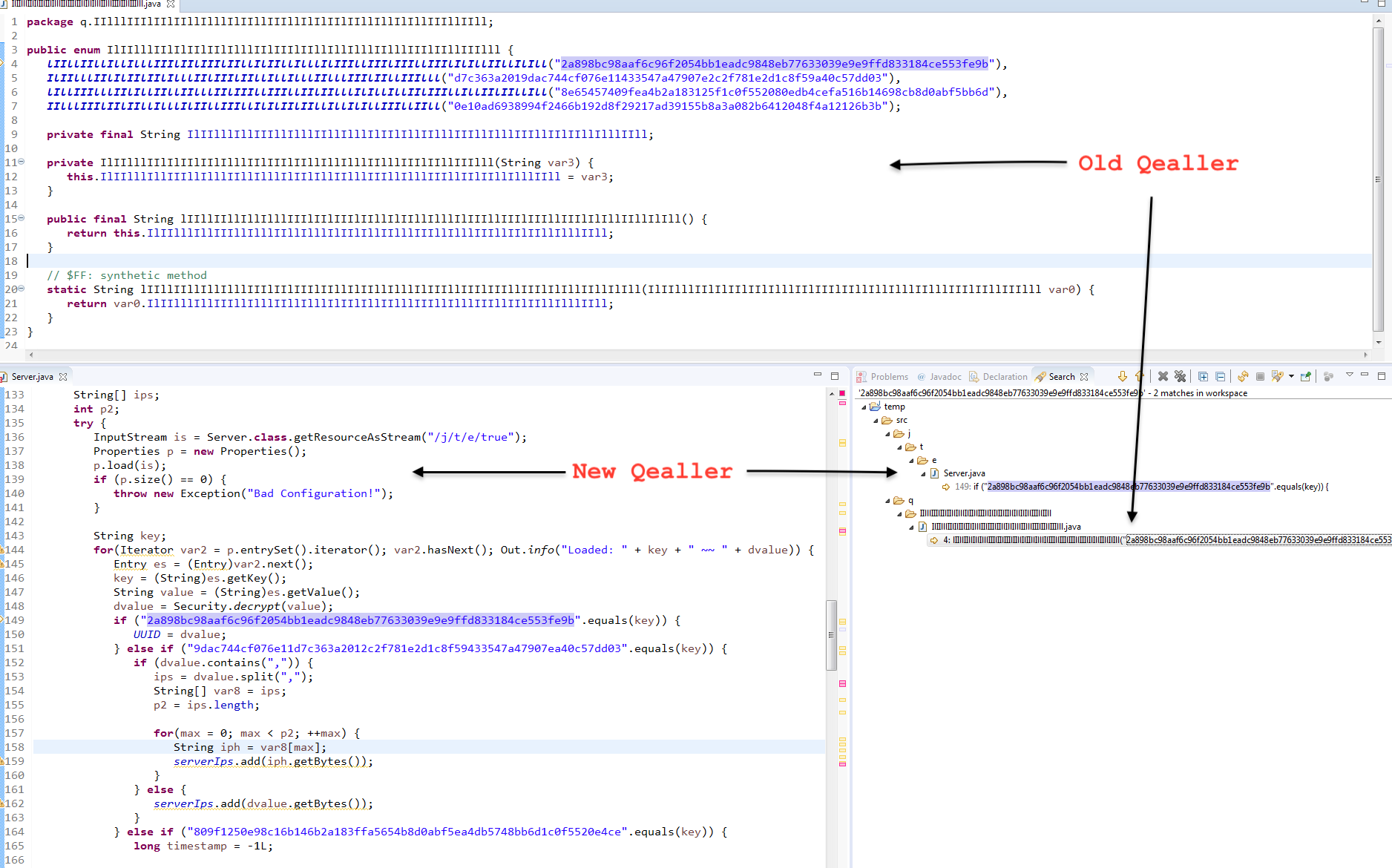
2. UUID Key 2a898bc98aaf6c96f2054bb1eadc9848eb77633039e9e9ffd833184ce553fe9b
Config is stored in a key value pair and key for UUID present in both variants. This key is also present in the Old Qealler Unloaded[2] article and the same string “Loaded:” is used in both variants.
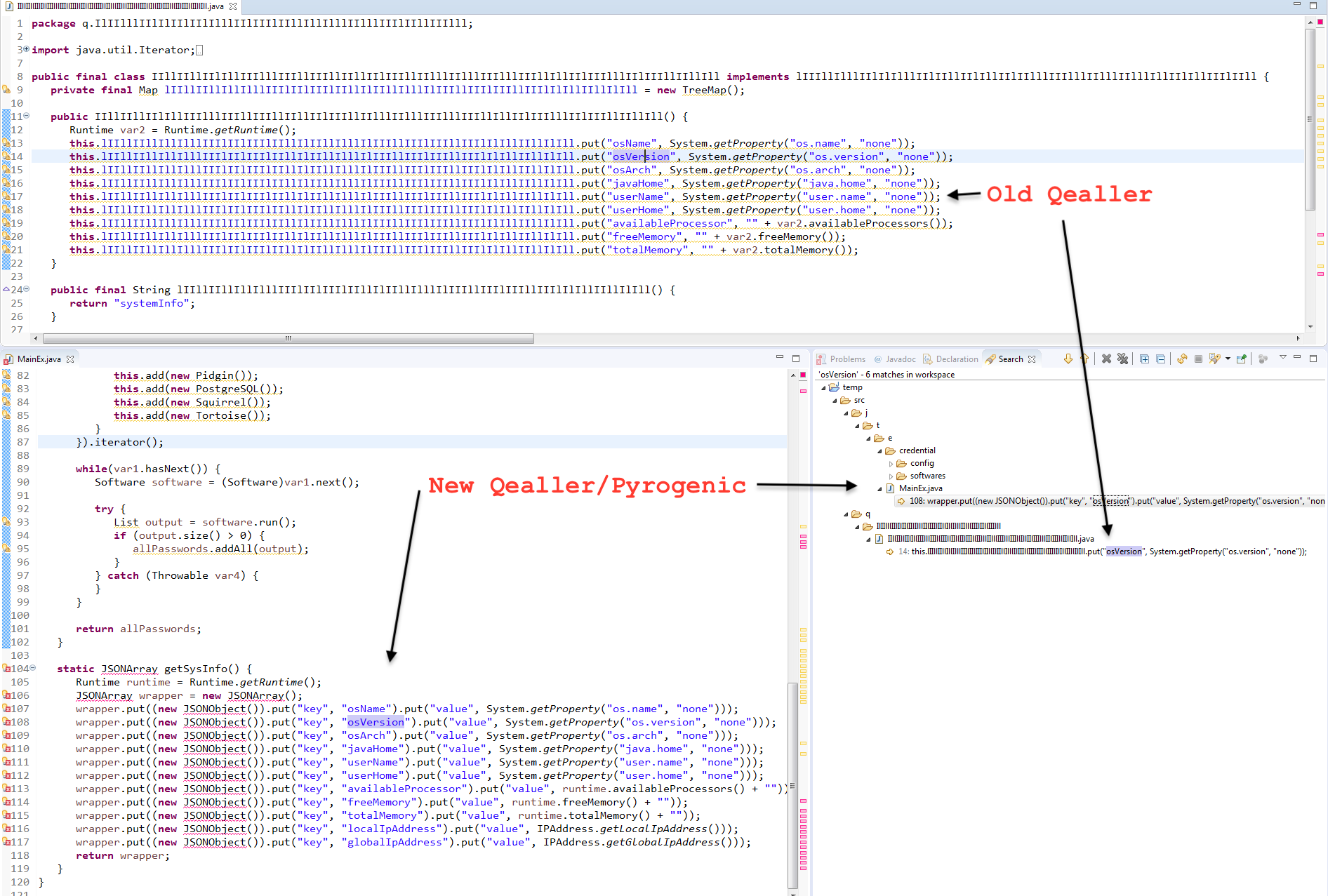
3. Systeminfo in JSON format
It collects the system info in JSON format before encrypting and sending it to CC. Both Qealler variants use the same key e.g osName, osVersion, osArch, totalMemory and code structure as shown below. localIpAddress & globalIpAddress keys are added to the new Qealler version.
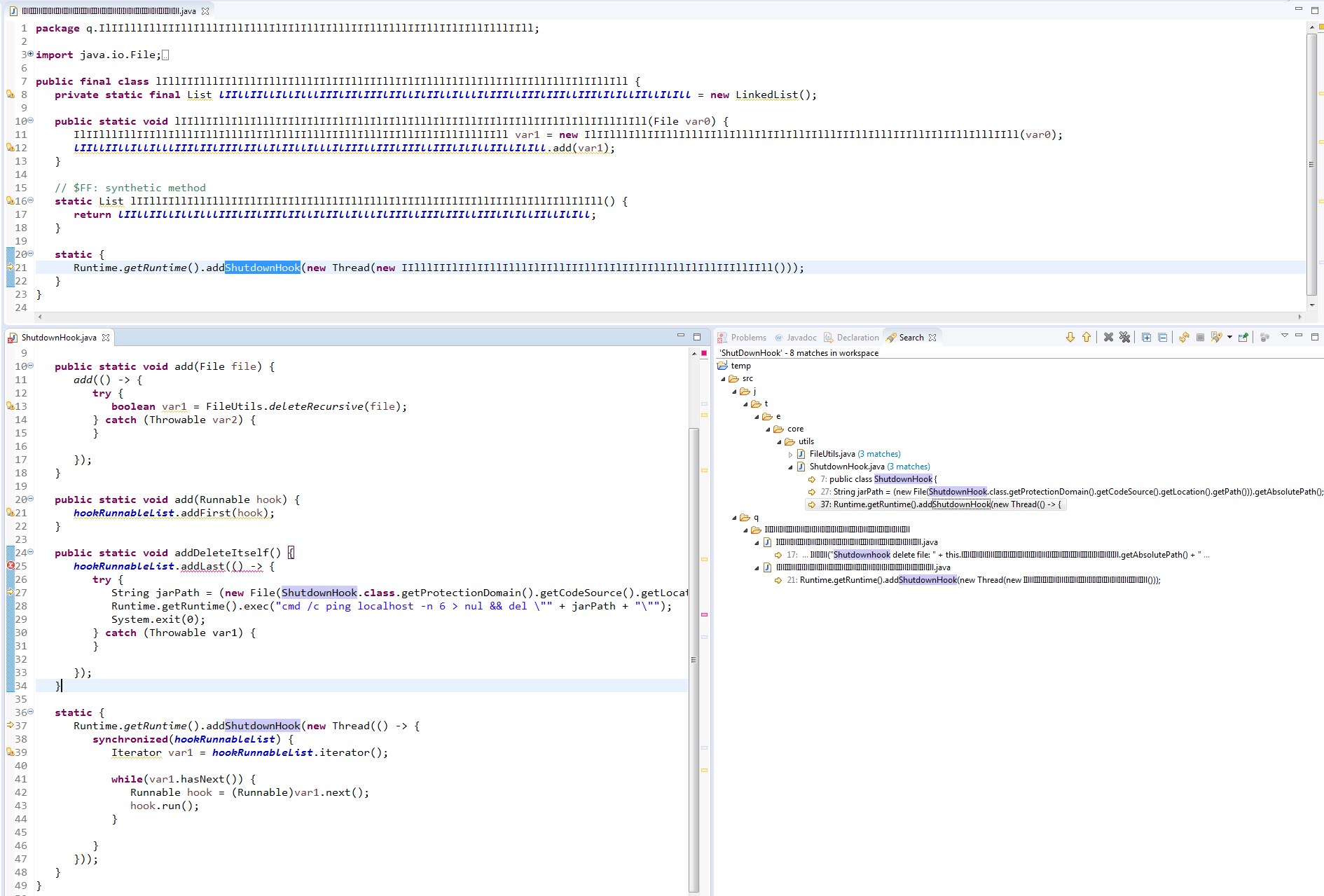
4. ShutdownHook
It is used when we want to run some code when JVM is shutting down and both variants use the addShutdownHook() to delete the files.
5. QeallerV4 string
Found this string “obfuscated/META-INF/QeallerV4.kotlin_module” in memory in the new Qealler/Pyrogenic sample. Maybe this is version 4 ?
Conclusion
In this Java malware analysis series we started with static analysis, then moved to Unpacking code using Java agent and in this last part we compared the Qealler variant. These above similarities are the most significant which I can find based on code analysis. I can conclude that the Malware author moved the Credential stealing from Python to Java based code. Malware authors are experienced coder as they divided the source code in multiple sensible packages and gave proper name to functions, variables and classes.
References
- Tweet by @James_inthe_box – (MD5: 65ab1ef8e9cef5c489d4b01cbb8a2a22) First Old Qealler tweet Aug 2018
- Qealler Unloaded by @jeFF0Falltrades – Sep 2018
- Qealler – a new JAR-based information stealer – Feb 2019
- ANY.RUN – (MD5: 65ab1ef8e9cef5c489d4b01cbb8a2a22) Old Qealler June 2018
- ANY.RUN – (MD5: 8D564A18B902461C19936CCB1F4E2F12) Old Qealler Sep 2018
- ANY.RUN – (MD5: F0E21C7789CD57EEBF8ECDB9FADAB26B) New Qealler/Pyrogenic Nov 2019
3 Comments. Leave new
[…] of the dumped Pyrogenic/Qealler source code to understand the stealer functionality. In the last part 0x3 we find similarity between Qealler/Pyrogenic variants based on static code analysis. Hope you […]
Thanks regarding offering these kinds of terrific content.
[…] static analysis, next part 0x2 we learn unpacking using Java agent and in the last part 0x3 we find similarity between Qealler/Pyrogenic variants based on static code analysis . You may […]