In the realm of malware analysis, tools like CyberChef play a pivotal role. One of the challenges that malware analysts often face is decrypting configurations of Remote Access Trojans (RATs) like AsyncRAT. This article provides a step-by-step guide on how to decrypt AsyncRAT configurations using CyberChef.
Decrypting AsyncRAT Configurations
AsyncRAT is a notorious RAT that enables attackers to remotely control infected systems. Decrypting its configurations can be a daunting task, but with the right tools and techniques, it’s achievable.
For those keen on exploring more about config decryption techniques, I recommend diving into my previous article.
CyberChef Recipe for AsyncRAT config decryption
Regular_expression('User defined','public static string \\w+\\s+\\=[ "0-9a-zA-Z+/=]{12,}',true,true,false,false,false,false,'List matches')
Find_/_Replace({'option':'Simple string','string':'public static string '},'',true,false,true,false)
Register('([\\s\\S]*)',true,false,false)
Comment('Input: In the filter operation box below, add the variable name that stores the AES key, e.g. Key')
Filter('Line feed','',false)
Regular_expression('User defined','(?<=\\")(.+?)(?=\\")',true,true,false,false,false,false,'List matches')
Register('([\\s\\S]*)',true,false,false)
Comment('Input: If you don\'t know the salt value, then try using the following salts. Don\'t forget to select the proper salt format HEX or UTF8.\n\nI have encountered only 2 salts for AsyncRAT:\n\nbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 (Format: HEX)\n\nDcRatByqwqdanchun (Format: UTF8)')
Derive_PBKDF2_key({'option':'Base64','string':'$R1'},256,50000,'SHA1',{'option':'Hex','string':''})
Register('([\\s\\S]*)',true,false,false)
Find_/_Replace({'option':'Regex','string':'.*'},'$R0',false,false,false,true)
Comment('Input: In the filter operation box below, add the variable name that stores the AES key, e.g. Key')
Filter('Line feed','',true)
Subsection('(?<=\\")([0-9a-zA-Z+/=]{32,})(?=\\")',true,true,false)
Fork('\\n','\\n',false)
From_Base64('A-Za-z0-9+/=',true,false)
To_Hex('None',0)
Drop_bytes(0,64,false)
Register('(.{32})(.*)',true,false,false)
Drop_bytes(0,32,false)
AES_Decrypt({'option':'Hex','string':'$R2'},{'option':'Hex','string':'$R3'},'CBC','Hex','Raw',{'option':'Hex','string':''},{'option':'Hex','string':''})
Merge(true)
Find_/_Replace({'option':'Regex','string':'$'},'\\nAES_KEY = "$R2"',false,false,false,true)
Input required
- The AsyncRAT line of code which contain encrypted setting
- Salt
-
bfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 (Format: HEX)
-
DcRatByqwqdanchun (Format: UTF8)
-
- The variable name that stores the AES key
Md5: 37e965330586a51125db2a420917db17
Follow the steps below to decrypt AsyncRAT configurations:
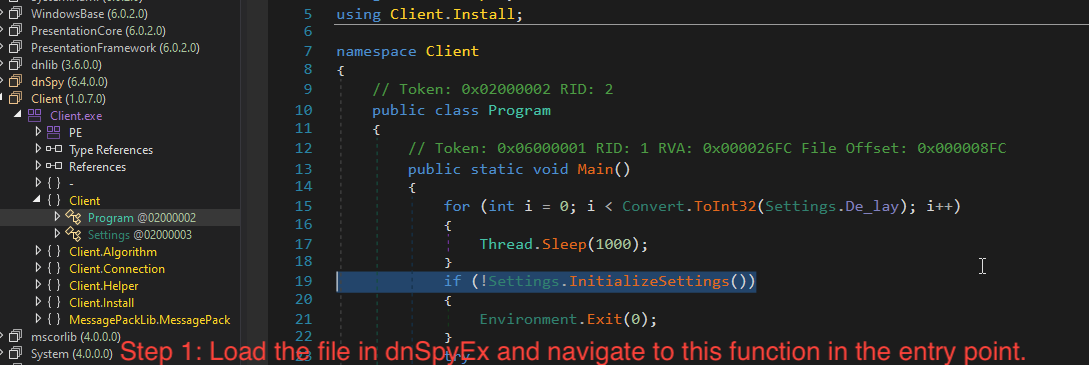
Step 1
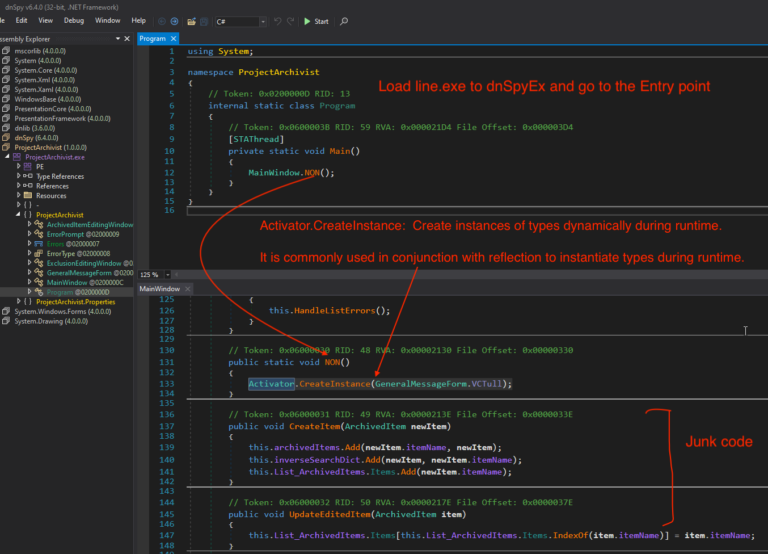
Load the file in dnSpyEx. After loading the assembly, right click & select ‘Go to Entry point‘. Navigate to the first function present inside if () i.e. Settings.InitializeSettings(). Click on this function to navigate to the definition of this function in the Settings class.
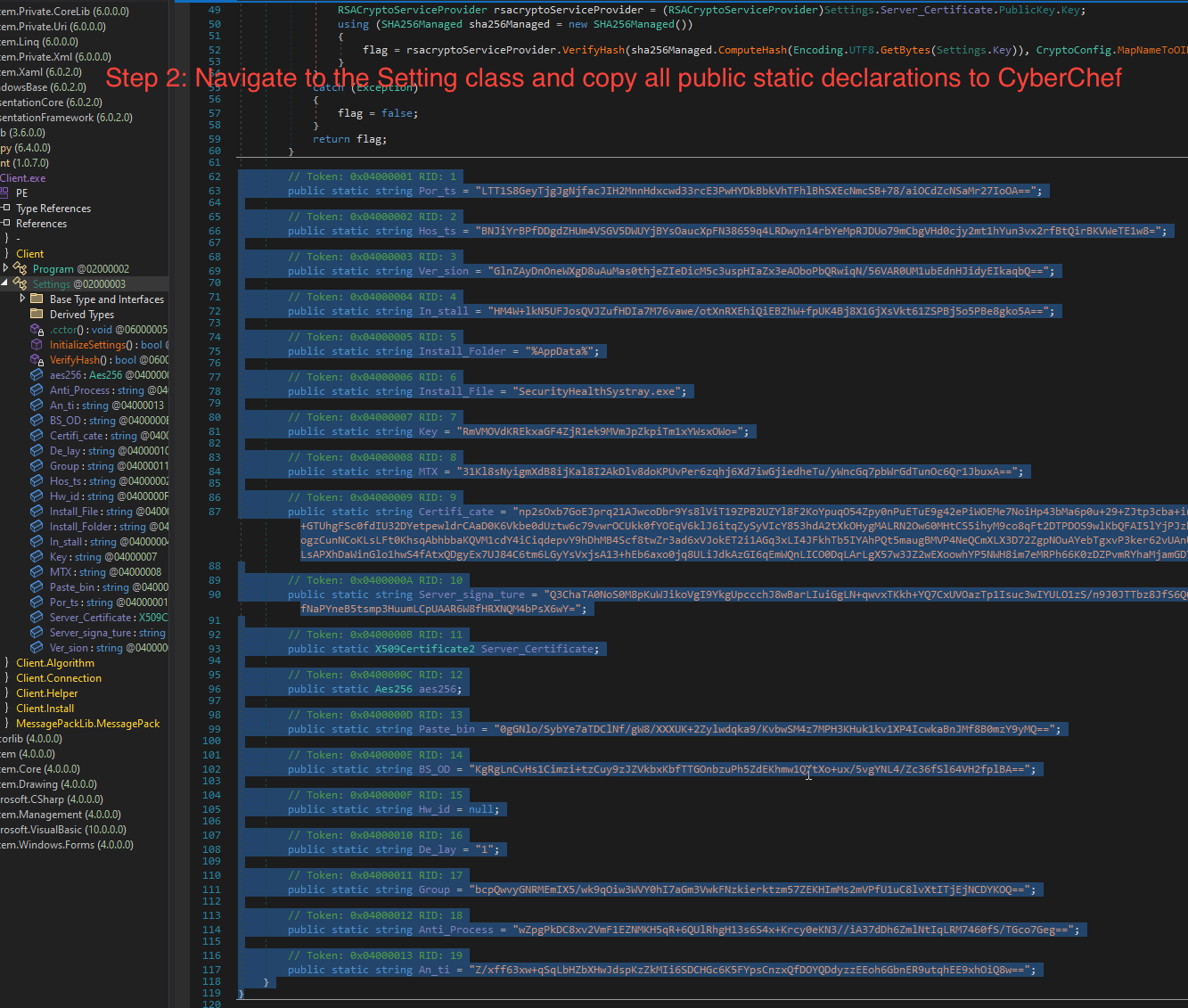
Step 2
Navigate to the Setting class and copy all public static declarations to CyberChef.
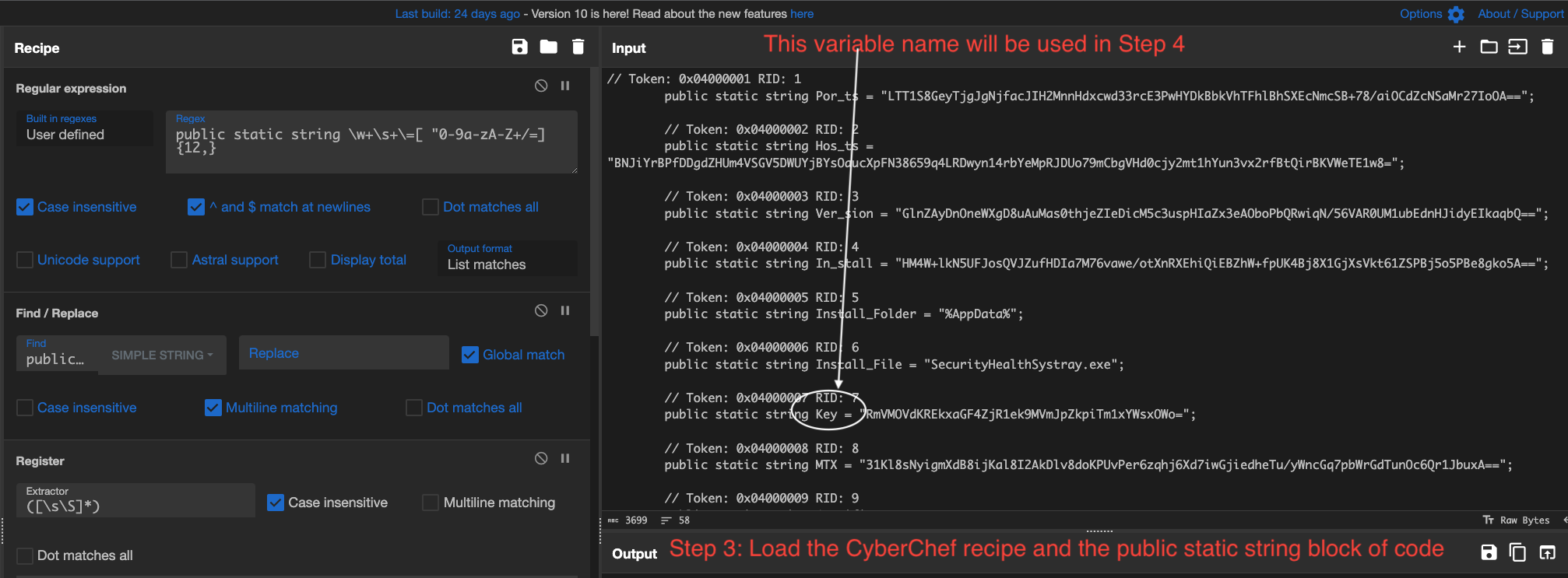
Step 3
Load the CyberChef recipe and the public static string block of code. The variable name ‘Key’ will be used in Step 4
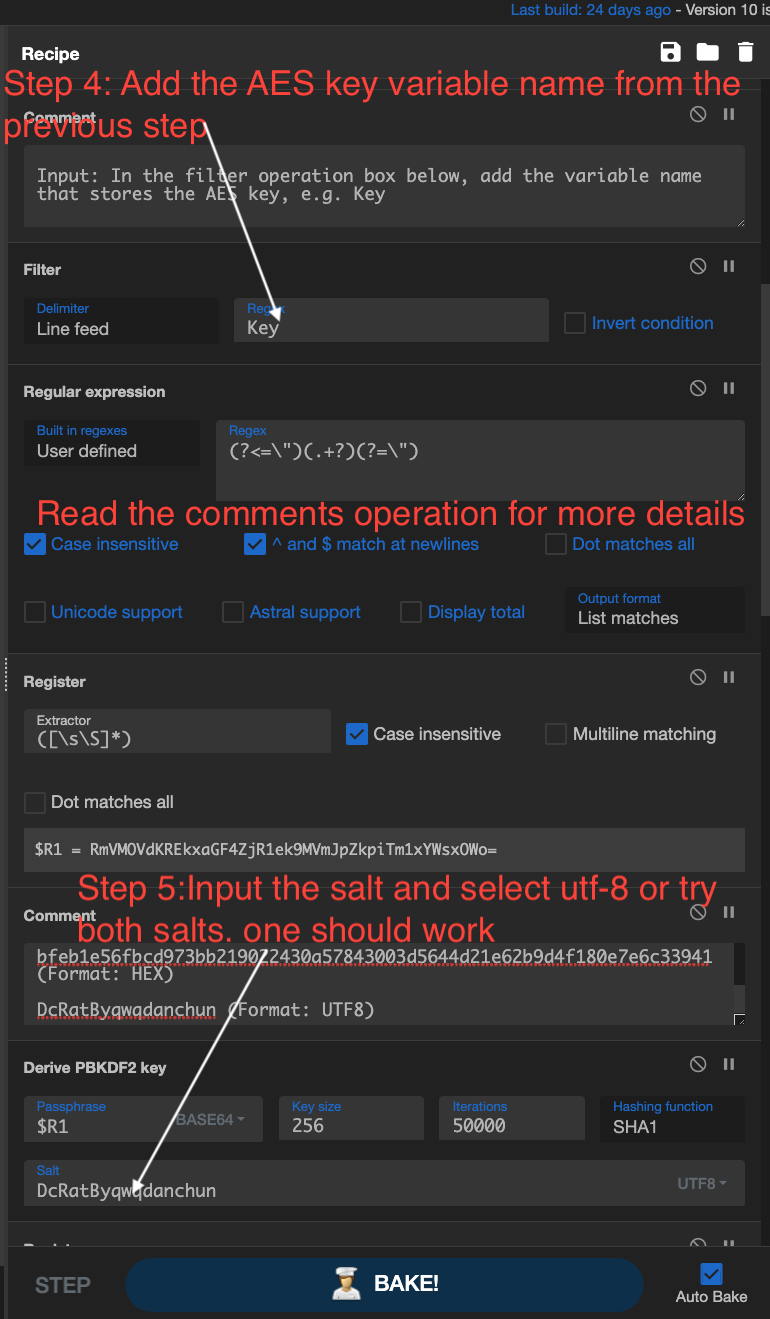
Step 4
Add the AES key variable name from the previous step. Note: Comments have been added in this CyberChef recipe for clarity.
Step 5
Input the salt and select utf-8, or try both salts, one should work. For more details read the comment in the recipe.
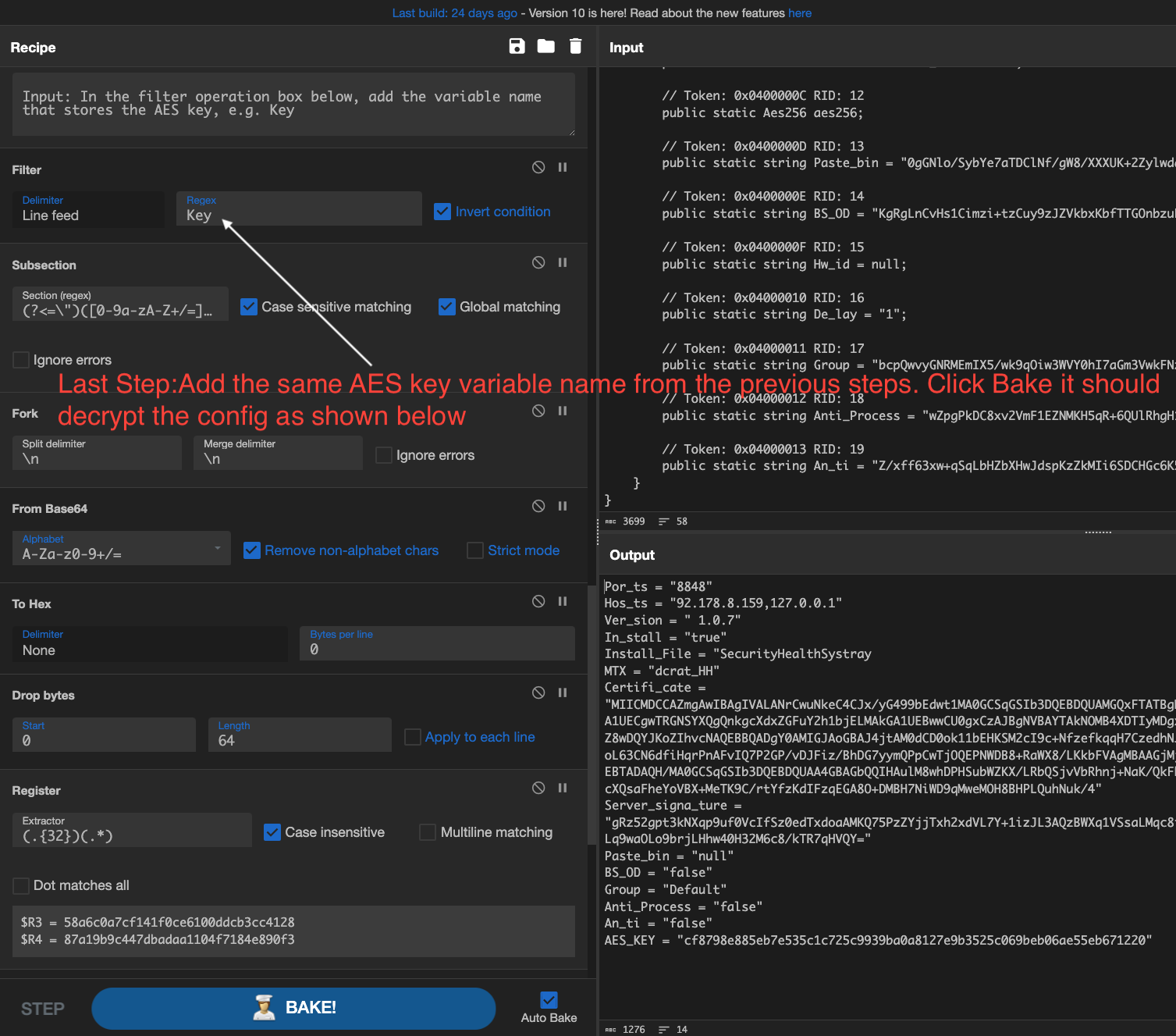
Last Step
Add the same AES key variable name from the previous steps. Click ‘Bake’; it should decrypt the config.
Conclusion
Decrypting AsyncRAT configurations can be a complex task, but with the right tools and recipes, it becomes manageable. CyberChef, with its versatile set of operations, is an excellent tool for this job. We hope this guide helps you in your malware analysis endeavors, especially when dealing with AsyncRAT.
Note: This recipe was initially developed by Srujan Kumar. I have made few modifications to support the new AsyncRAT files.