Malware Analysis
UAC bypass analysis (Stage 1) Ataware Ransomware – Part 0x2
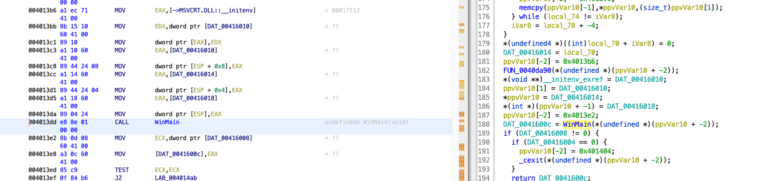
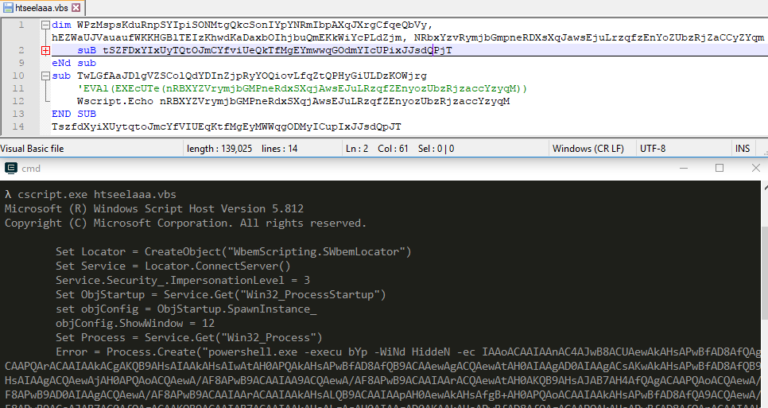
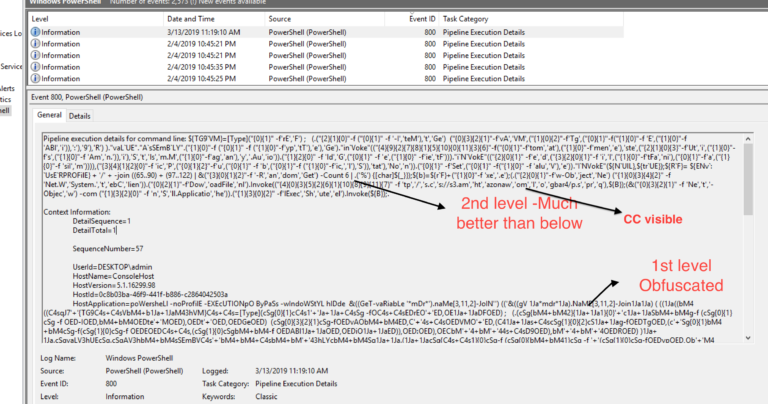
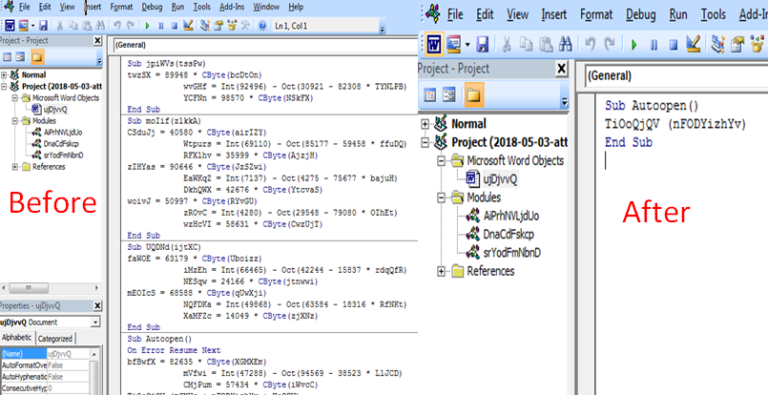
Ataware Ransomware uses UAC bypass using CMSTPLUA COM interface in ATAPIinit.exe (Stage 1). It was downloaded from Dropbox url when the user opened the malicious Excel and enabled the Macro. For details, please check the previous Excel 4.0 Macro Analysis – Ataware Ransomware Part 1. You may download the ATAPIinit.exe…
Read More